Unimus performs backups as per the schedule configured for the device.
The device needs to first be discovered (see the Discovery article) before it can be backed-up.
Unimus will use the discovered connector (protocol/port combination) and the discovered credentials to connect to the device.
After a successful connection, config of the device is retrieved, and stored.
Unimus can handle logging in to the device in user-exec or privileged-exec mode.
(if the particular device has concepts of "user-exec" / "privileged-exec")
If the device needs to be switched into privileged-exec, Unimus will do so.
(the "enable" password was already discovered during Discovery)
Unimus will retrieve the configuration from the device using the appropriate commands for each vendor automatically.
If the device has concepts of "startup-config" / "running-config", Unimus always works with the "running-config" of the device.
If the device does not have concepts of "startup-config" vs. "running-config", Unimus will simply retrieve a backup.
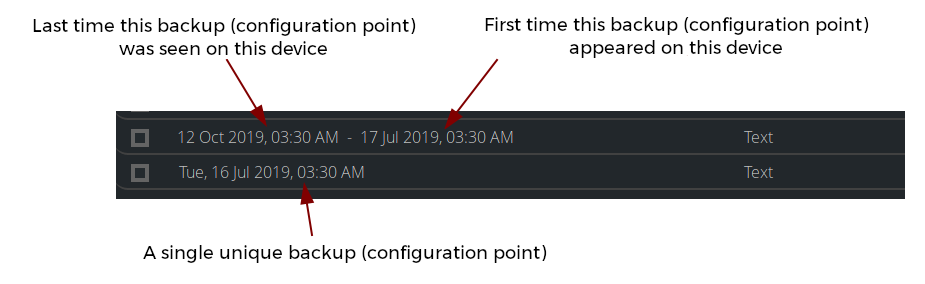
Starting with version 1.6.0, Unimus automatically stores only unique backups of the config.
If a backup retrieved from the device is the same as the last backup already in the system, it will not be stored.
The backups table will show a time range for which a backup was valid for, rather than just backup retrieval timestamp.
Dynamic data (such as timestamps, etc.) are automatically filtered from backups before Unimus compares backups to analyze if they have changed.
(this is supported for all our supported vendor drivers)
This feature makes it much easier to see when a device config changes.

Discovery
Scheduling
Backup Filters
Sensitive data stripping